laravel xss - Download Now Online
get free ebook now
how and where can xss protection be applied in laravel. also it is possible that xss attack could be a reflected attack where the displayed data is not coming from the database but from another source i e an uploaded file url etc if you fail to filter all the various input locations you run a risk of missing something laravel encourages you to escape all output regardless where it came from.
csrf protection laravel the php framework for web artisans. laravel automatically generates a csrf token for each active user session managed by the application this token is used to verify that the authenticated user is the one actually making the requests to the application anytime you define a html form in your application. xss filter in laravel framework a muhammad usman. xss filter in laravel framework if you are connected with the php development world then you must have heard the name laravel and you know what it is if you dona t know laravel is a modern php framework which utilizes modern php features and uses some of the existing frameworksa components to truly awesomify php development. laravel validation sanitization to prevent xss exploits. xss exploit is a well known vulnerability in a web app whereby an attacker can inject client side code into a web page this is can be done through user input a learn how to prevent xss injection attack using laravel validation and input sanitization learn how to prevent xss injection attack using laravel validation and input sanitization. php how can you apply xss filters in laravel 4 framework. how do you think about security in laravel 4 i mean how laravel is managing xss attacks in codeigniter you have someting like xss clean get yourvalue to clean user input fom xss code how laravel manage those kind of problems you get user values using input get yourvalue but how do you apply an xss filter to it. github gvlatko laravel xss a port of codeigniter. laravel xss a port of codeigniter security library to laravel for xss prevention installation include the package in your composer file require gvlatko laravel xss dev master run composer update add the service provider in you app php config file in the providers array gvlatko laravelxss laravelxssserviceprovider.
blade templates laravel the php framework for web artisans. blade is the simple yet powerful templating engine provided with laravel unlike other popular php templating engines blade does not restrict you from using plain php code in your views in fact all blade views are compiled into plain php code and cached until they are modified meaning blade adds essentially zero overhead to your application. best laravel security features for your application. now if there is no xss protection in place the laravel vulnerabilities will increase as the javascript will execute every time the page reloads while the example code is not malicious in itself it is the perfect example that demonstrates the full extent of this attack laravel offers native support that protects the code from xss attacks. laravel 5 4 cross site scripting a packet storm. exploit title laravel non presistent xss in validation of arrays date 06 03 2017 exploit author mahdyfo mahdyfof the at sign gmail com vendor homepage laravel com version 5 4 in laravel validation rules assume that you set a rule to get an array input. how to create middleware for xss protection in laravel 5. xss filter through you can remove html tag from your input value and it is very important to remove html tag for security in your laravel 5 2 application you can implement by using middleware concept in your project so how to create xss filter middleware in your laravel application by using following step.
laravel auth,laravel api,laravel ajax,laravel admin,laravel array,laravel attach,laravel admin template,laravel api routes,laravel api resource,laravel api authentication,xss attack,xss attack example,xss attack sample,xss attack tutorial,xss access denied bypass,xss attack prevention,xss attack example php,xss alert,xss auditor,xss and csrf








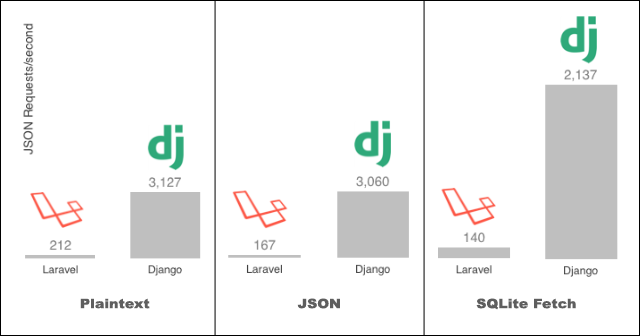



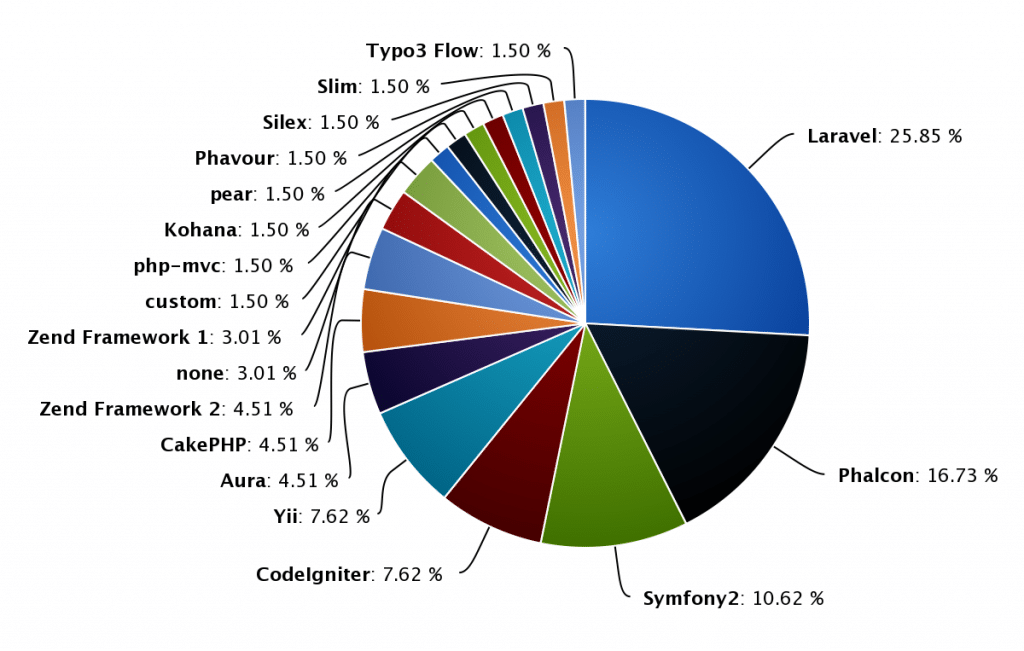
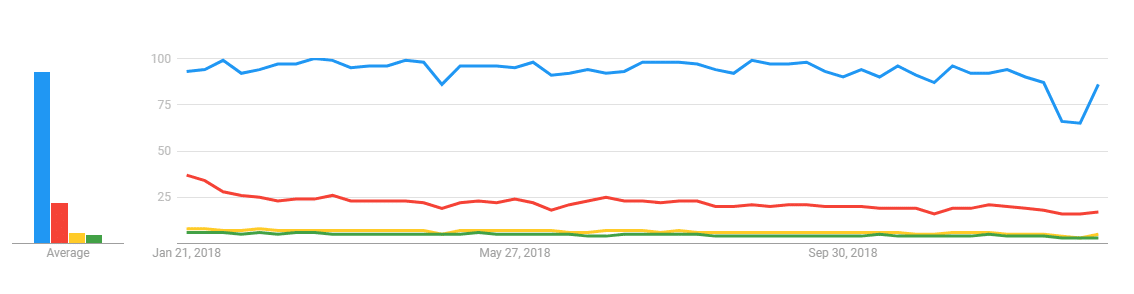













![XECon2015 :: [2-1] 정광섭 - 처음 시작하는 laravel](https://image.slidesharecdn.com/random-151116001443-lva1-app6892-2-160323043830/95/xecon2015-21-laravel-38-638.jpg?cb=1458707958)




No comments:
Post a Comment